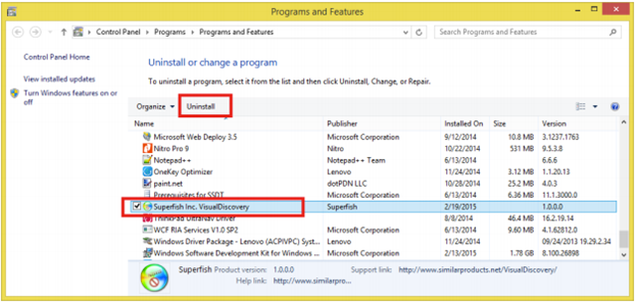
It looks like a never end story. From Xiaomi smartphones and now to Lenovo, both Chinese manufacturers. According to reports from various media, customers were noticing strange sponsored links while doing searches on their PC. The user later found out that it is the works of a piece of program residing and preloaded in the system. It is called “SuperFish”. As it names implies, it seems to be meant for FISHING out information and supplying ads. #SuperFish
Screenshot: Courtesy of @KennWhite
The most shocking truth is that it supplies certificates that certificate is valid through 2034, 1024-bit, SHA-1 is absurd for 20 years. So, in this case, when you are accessing www.bankofamerica.com, you are actually using a certificate issued by SuperFish, Inc instead of VeriSign or some authentic issuer. I wonder where does your SSL traffic go to.
When contacted by Engadget, Lenovo says that has not found “any evidence to substantiate security concerns.” The manufacturer did want to make one thing abundantly clear in a statement given to Engadget:
“Superfish technology is purely based on contextual/image and not behavioral. It does not profile nor monitor user behavior. It does not record user information. It does not know who the user is. Users are not tracked nor re-targeted. Every session is independent.”
While some users are not concern about privacy. “Oh I have nothing to hide”. Well, it is really up to oneself to secure your own system. Cases of such violation is rampant these days when everyone is using all means to gather or even exploit user gathered information, your behavioral patterns. In this case, it is a total replacement of your SSL transaction to a strange Certification Authority, that is really big RED FLAG.
If you are using a Lenovo notebook or PC, use malwarebytes to clean your system. You might need to use regedit to remove SuperFish from the Certmgr.msc
(certificate manager).