NETSTAT is a powerful command-line tool that can be used to view all active network connections on your PC. This can be helpful for troubleshooting network problems, but it can also be used to detect suspicious activity that may indicate that your PC has been compromised.
Here are some detailed steps on how to use NETSTAT to check for suspicious activity:
- Open a command prompt window.
- Type the following command and press Enter:
netstat -ano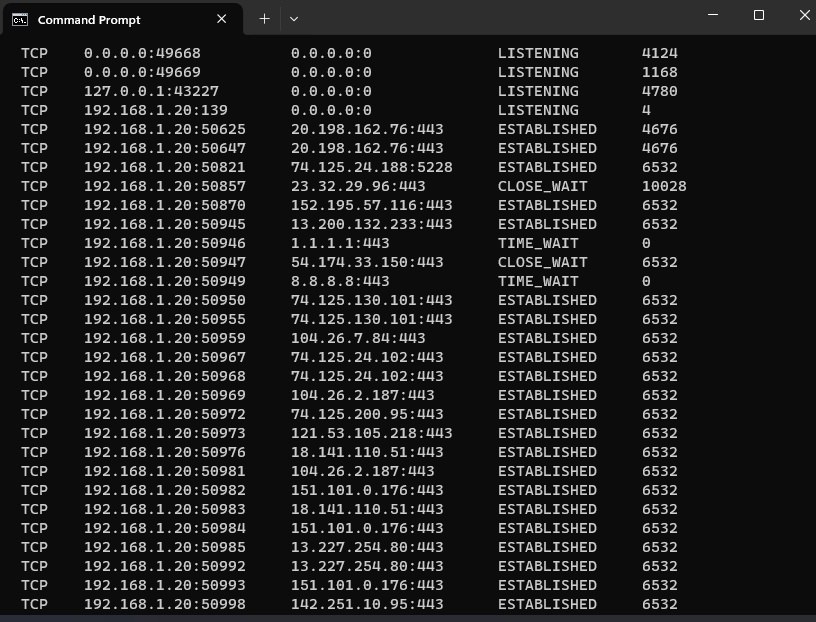
This will display a list of all active network connections, including the following information:
- Protocol: TCP or UDP
- Local address and port: The IP address and port number of your PC
- Remote address and port: The IP address and port number of the remote computer that you are connected to
- State: The state of the connection, such as ESTABLISHED, LISTENING, or TIME_WAIT
Review the list of connections for any suspicious activity. Here are some things to look for:
- Connections to unknown IP addresses or ports: If you see connections to IP addresses or ports that you don’t recognize, this could be a sign that your PC has been compromised. You can use a service like IPWhois to get more information about an IP address.
- Connections to high-risk countries or regions: Some malware is known to communicate with servers in high-risk countries or regions, such as Russia and China. If you see connections to these countries or regions, this could be a sign of infection.
- Connections to known malware domains: There are a number of websites that are known to be used by malware to communicate with its command and control servers. If you see connections to any of these websites, this is a strong indication that your PC is infected.
- Connections that are using a lot of bandwidth: If you see connections that are using a lot of bandwidth, this could be a sign that malware is sending or receiving a large amount of data.
- Connections that are in a strange or unexpected state: Some malware may try to hide itself by using unusual or unexpected connection states. For example, you may see connections in the TIME_WAIT state that are not closing properly.
If you see any suspicious connections, you can try to identify the process that is associated with the connection using the following command:
netstat -ano | findstr <process_name>
This will display all of the connections that are associated with the specified process. If you don’t recognize the process, or if it’s a process that you’re not familiar with, it’s best to err on the side of caution and terminate the process.
Keep in mind that NETSTAT can’t detect all malicious activity. Some malware is designed to hide itself from NETSTAT. However, NETSTAT is still a useful tool for detecting suspicious activity on your PC.
Here are some additional tips for using NETSTAT to check for a compromised PC:
- Compare the output of NETSTAT to a known-good baseline. This will help you to identify any new or unexpected connections. You can create a known-good baseline by running NETSTAT on your PC when it is in a clean state.
- Use a network monitoring tool to track network traffic over time. This can help you to identify any unusual spikes in traffic or suspicious patterns. There are a number of free and paid network monitoring tools available.
- Keep your software up to date, including your operating system, security software, and antivirus software. This will help to protect you from the latest known vulnerabilities.
If you’re concerned that your PC may have been compromised, you should run a full system scan with your antivirus software. You should also consider changing your passwords for all of your online accounts.


